Blog
- Home
- Blog

How Energy IT Support Can Transform Your Operations: 10 Powerful Steps to Success
The energy sector is rapidly evolving, and so are the technological demands that power its operations. To keep up, efficient IT support is no longer

Exposing 15 Cybersecurity Misconceptions: Separating Myths from Reality
In the ever-evolving world of cybersecurity, myths and misconceptions abound. But believing these can leave individuals and businesses vulnerable. That’s why exposing 15 cybersecurity misconceptions

How Do You Think Digital Access Impacts Various Areas of Cybersecurity? 10 Key Threats and Solutions
As digital access expands, so do the challenges it presents in cybersecurity. But how do you think digital access impacts various areas of cybersecurity? From

How Can Generative AI be Used in Cybersecurity? 10 Smart Ways to Stay Ahead of Threats
In today’s fast-evolving digital landscape, cyber threats are becoming more sophisticated. But how can generative AI be used in cybersecurity to counter these risks? Generative

How to Get Into Cybersecurity: 6 Powerful Steps to Launch Your Career
With cyber threats on the rise, a career in cybersecurity is more in demand than ever. But how to get into cybersecurity may seem daunting

12 Major Challenges in Banking IT Support and How to Overcome Them Effectively
Managing Banking IT Support comes with a unique set of challenges. From ensuring cybersecurity to maintaining system uptime, the complexities of financial technology can stretch
How Does the Issue of Cybersecurity Relate to the Internet of Things? 10 Types of IoT Cyber Security Attacks
As smart devices become a part of daily life, they bring both convenience and new threats. But how does the issue of cybersecurity relate to

15 Major Online Activities That Expose You to the Highest Cybersecurity Risks
The internet offers endless opportunities, but it also comes with risks. Certain online activities expose you to the highest cybersecurity risks, making your personal data
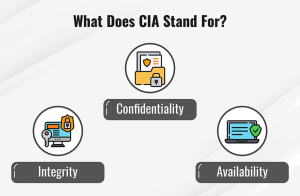
In Cybersecurity, What Does CIA Stand For? Unlock the 5 Major Benefits of the CIA Triad
When it comes to cybersecurity, a strong foundation is essential. But in cybersecurity, what does CIA stand for? The CIA Triad—Confidentiality, Integrity, and Availability—forms the

What is the Median Salary of a Cybersecurity Engineer? Discover 10 High-Paying Cities in the USA for 2025
In the world of cybersecurity, demand for skilled engineers is skyrocketing, and with that comes competitive salaries. But what is the median salary of a

15 Major Benefits of Outsourcing Banking IT Support
In the fast-paced world of finance, having reliable Banking IT Support is crucial for smooth operations. But managing IT in-house can drain resources and time

How Banking IT Support Transforms Operations: 10 Proven Ways
The banking industry is all about efficiency and security, and that’s where Banking IT Support plays a crucial role. From streamlining daily operations to enhancing

How to Choose the Right Manufacturing IT Support Provider in 12 Proven Steps
Finding the right Manufacturing IT Support provider can be the key to unlocking smooth operations and staying ahead of the competition. But with so many

15 Essential Best Practices for Manufacturing IT Support in Small Operations
Managing IT in a small manufacturing operation comes with unique challenges. From limited resources to maintaining system efficiency, Manufacturing IT Support requires a tailored approach

Overcome 12 Major Challenges in Manufacturing IT Support
Manufacturing IT Support comes with its own unique set of hurdles. From keeping systems up-to-date to ensuring smooth production flows, it can feel like a

Discover 15 Major Benefits of Outsourcing Manufacturing IT Support
Managing IT in-house can be a major challenge for manufacturing businesses. That’s why many are turning to outsourcing Manufacturing IT Support to streamline operations and


